but I suspect something will come along to address these issues and snatch the market away from Flatpak.
I believe it could only be fixed by a team from GNOME or KDE, they're the one in a position to develop something like Flatpak but deeply integrated with the system instead of trying to get around it.
For what's worth Apple did a very good job when it came to the isolation and containerization of desktop applications, but again only possible because they control both sides.
Apple enforces a LOT of isolaton, they call it sandboxed apps and it is all based on capabilities, you may enjoy reading this. Applications get their isolated space at ~/Library/Containers and are not allowed to just write to any file system path they want.
A sandboxed app may even think it is writing into a system folder for preference storage for example - but the system rewrites the path so that it ends up in the Container folder instead. For example under macOS apps typically write their data to ~/Library/Application Support. A sandboxed app cannot do that - and the data is instead written beneath the ~/Library/Containers/app-id path for that app.
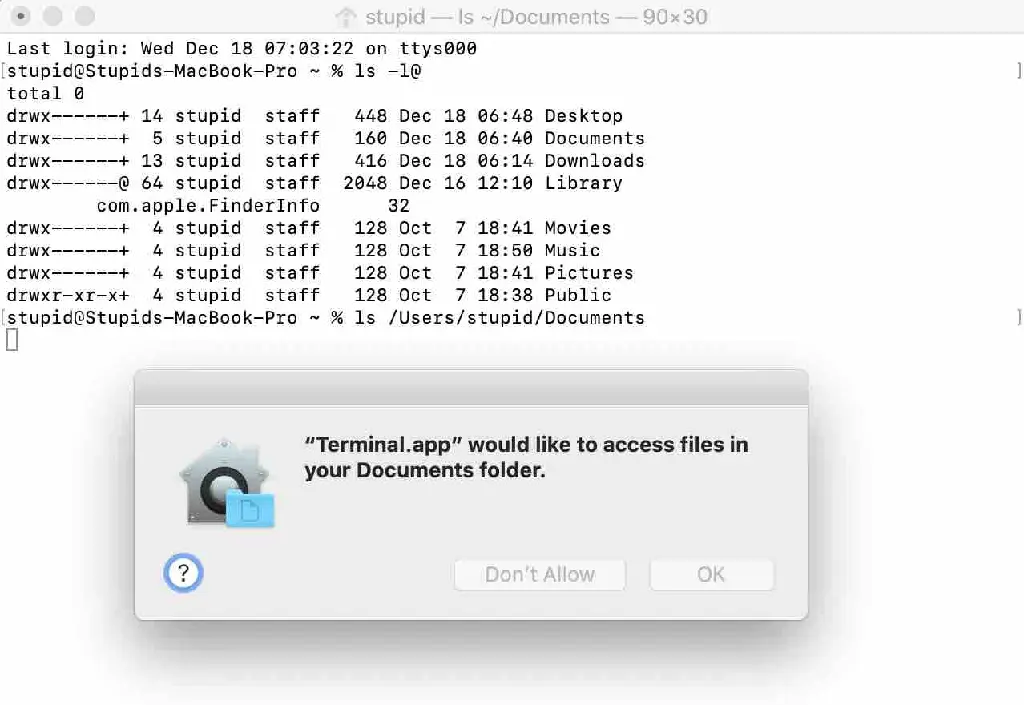
And here's how good Apple is, any application, including 3rd party tools running inside Terminal will be restricted:
I bet most people weren't expecting that a simple ls would trigger the sandbox restrictions applied to the Terminal application. The best part is that instead of doing what Flatpak does (just blocking things and leaving the user unable to to anything) the system will prompt you for a decision.
I believe this was the best way to go about things but it would require to get a DE team to make it in a cohesive and deeply integrated with the system. Canonical could do it... but we all know how Canonical is.